I recently had to configure Cisco SNMP data into Splunk, so thought this might help, on how I did it. I was lucky enough to come across this very good Splunk article on SNMP data into ITSI – so a Big up to Liz Snyder https://www.splunk.com/en_us/blog/it/managing-snmp-traps-with-itsi-event-analytics.html I used info in here and made some adjustments for my environment which gave me a good head start, why re-invent the wheel, just pimp it up or Splunk it UP!!
My changes were to change the host name so it comes from the device, add some CIM mapping, and send the header data on restart to null.
My environment:
Linux Centos 8 / Splunk 8.5
Step 1 Install and Configure SNMP
sudo yum install net-snmp net-snmp-utils
sudo systemctl enable snmpd
sudo systemctl enable snmptrapd
sudo systemctl start snmpd
sudo systemctl status snmpd -l
sudo snmpwalk -v 2c -c public -O e 127.0.0.1
Step 2 Make snmp log file
mkdir /snmp
cd /snmp
sudo touch ./traps.log
sudo setfacl -R -m u:splunk:rx /snmp/traps.log
Step 3 Config SNMPD conf
This will load the snmpd config and all the MIBS and point to the log file called traps.log
vi /etc/sysconfig/snmptrap
OPTIONS=”-c /etc/snmp/snmptrapd.conf -A -n -Lf /snmp/traps.log -OQ -m +ALL –disableAuthorization=yes -p /var/run/snmptrapd.pid”
Step 4 Config SNMTRAPD conf
This formats the SNMP data
vi /etc/snmp/snmptrapd.conf
# snmptrapd formatting
#http://www.net-snmp.org/wiki/index.php/TUT:Configuring_snmptrapd_to_parse_MIBS _from_3rd_party_Vendors
# SNMPV1
format1 Agent_Address = %A\nAgent_Hostname = %B\nDate = %y-%02.2m-%02.2l %02.2h:%02.2j:%02.2k\nEnterprise_OID = %N \nTrap_Type = %w\nTrap_SubType =%q\nCommunity_Infosec_Context = %P\nUptime = %T\nDescription =%W\nPDU_Attribute_Value_Pair_Array:\n%V\n%v\n—\n
# SNMPV2
format2 Agent_Address = %A\nAgent_Hostname = %B\nDate = %y-%02.2m-%02.2l %02.2h:%02.2j:%02.2k\nEnterprise_OID = %N\nTrap_Type = %w\nTrap_SubType = %q\nCommunity_Infosec_Context = %P\nUptime = %T\nDescription = %W\nPDU_Attribute_Value_Pair_Array:\n%V\n%v\n—\n
Step 5 Check and enable SNMP Services
sudo systemctl restart snmptrapd
sudo systemctl status -l snmptrapd
sudo systemctl enable snmpd
sudo systemctl enable snmptrapd
Step 6 Check MIBS
Check /usr/share/snmp/mibs this should have a load of mibs, should add any new ones into this folder from the Ciscos Web site
Step 7 Send some test traps
sudo snmptrap -v 2c -c public localhost ” 1.3.6.1.4.1.8072.2.3.0.1 1.3.6.1.4.1.8072.2.3.2.1 i 123456
sudo snmptrap -v2c -c public localhost 1 1
sudo tail -f /snmp/traps.log
You should see data, as the formatting is Key value pairs, this will get parsed easily
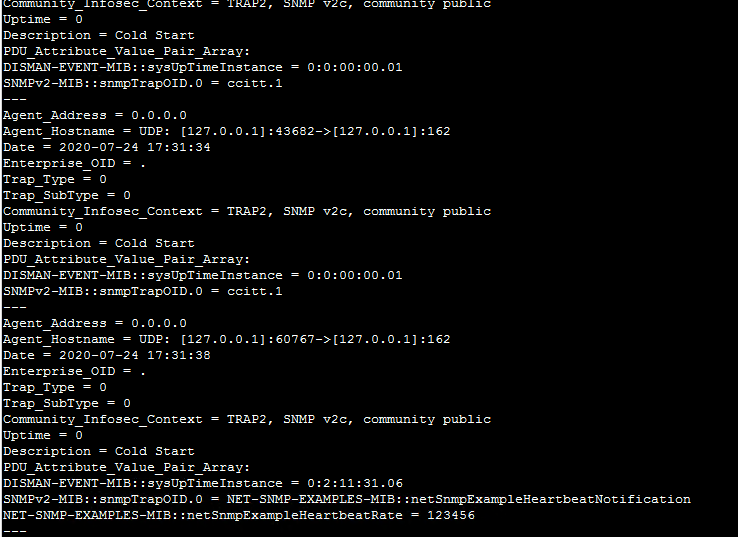
Step 8 Create Inputs / Props / Transforms conf
Inputs.conf
[monitor:///snmp/trapd.log]
disabled = false
index = snmptrapd
sourcetype = network:snmptrapd
Props.conf
[network:snmptrapd]
KV_MODE = auto
LINE_BREAKER = ([\r\n]+)Agent_Address\s=
MAX_TIMESTAMP_LOOKAHEAD = 30
NO_BINARY_CHECK = true
SHOULD_LINEMERGE = true
TIME_FORMAT = %Y-%m-%d %H:%M:%S
TIME_PREFIX = Date\s=\s
disabled = false
pulldown_type = true
TRANSFORMS-null = setnull
#Change host name
TRANSFORMS-hostname = snmpdevice
#Added For CIM Mapping
#Extract CIM Fields
EXTRACT-CIM-fields = Agent_Hostname\s=\s(?P<protocol>.+):.*\[(?P<src_ip>.+)\]:(?P<src_port>.+)->\[(?P<dest_ip>.+)\]:(?P<dest_port>.+)$
FIELDALIAS-dvc = src_ip AS dvc
EVAL-direction=”inbound”
EVAL-app=”SNMP”
#This sends unwanted data to null
Transforms.conf
[setnull]
REGEX = ^(NET.*)
DEST_KEY = queue
FORMAT = nullQueue
#This changes the host name
[snmpdevice]
REGEX = Agent_Address\s=\s(?P<snmpdvc>.+)
FORMAT = host::$1
DEST_KEY = MetaData:Host
Step 9 Generate more SNMP tests and you should see the trap in your snmptrapd index

